Training modules
Cyber Security Basic Methodologies & Forensics Training
This course is designed to immerse participants in a practical cybersecurity environment through a straightforward cybersecurity training program. The training employs a Red Team/Blue Team exercise, where the Red Team, consisting of offensive security experts, attempts to breach an organization’s cybersecurity defenses, while the Blue Team defends against and counteracts these attacks. The focus of this training is on the Blue Team perspective, emphasizing digital forensics methodologies to enhance defense strategies.


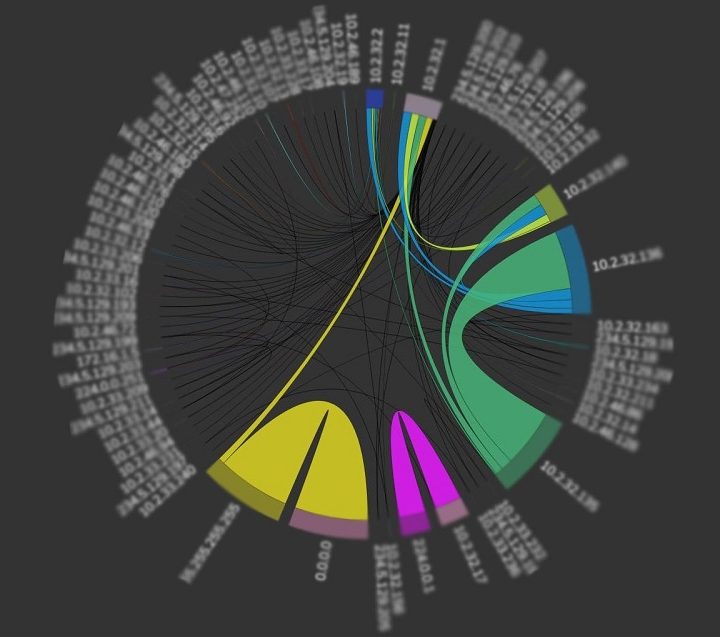
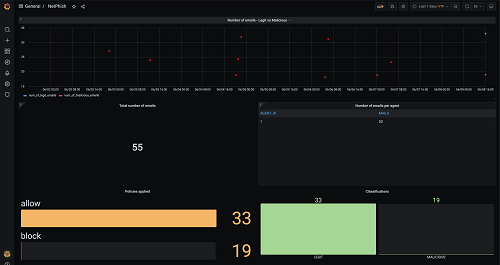
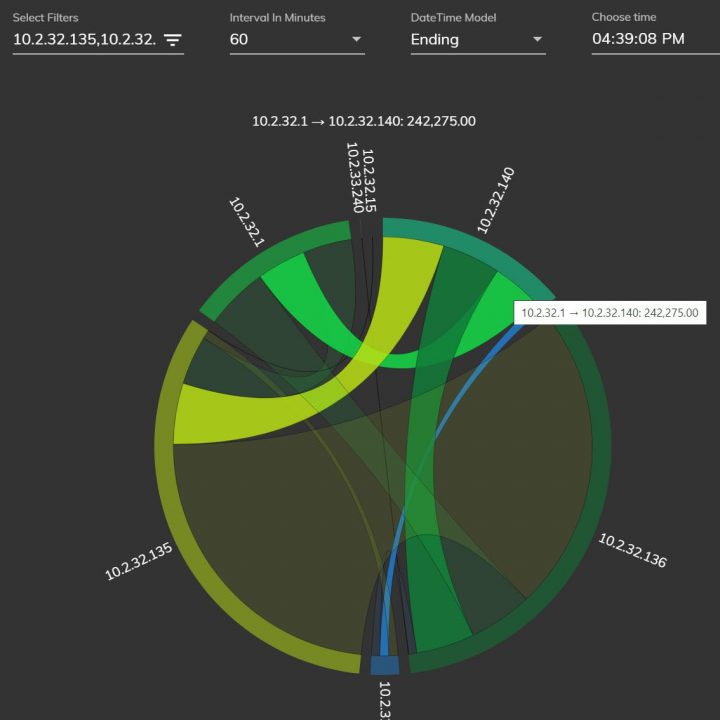
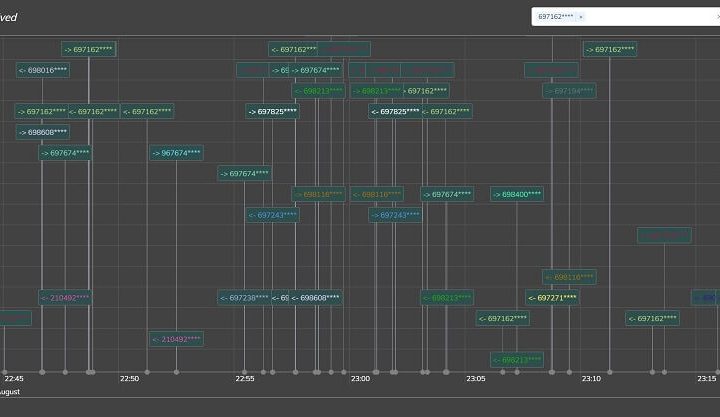
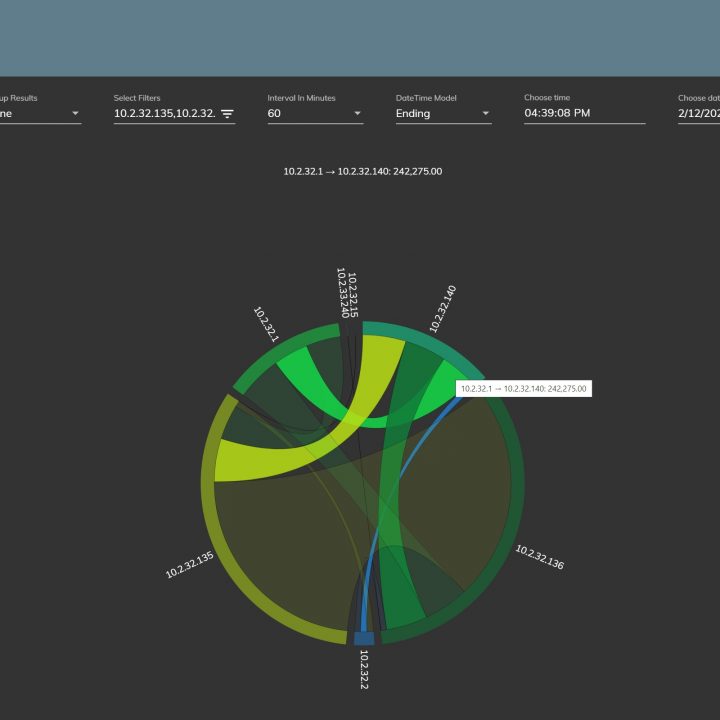
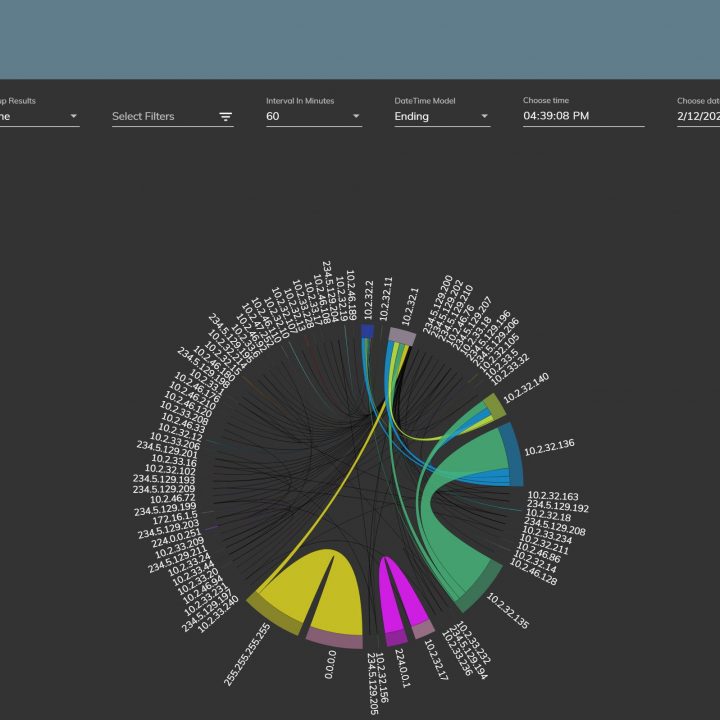
Digital forensics with SmartViz DMT
This course endeavors to provide users with a practical demonstration of SmartViz DMT, showcasing its functionalities in crucial cybersecurity domains including endpoint security, security training, reporting, security-focused design, and the detection of data manipulation. Additionally, it offers an in-depth exploration of SIEM (Security Information and Event Management) and its operational methods through digital forensics analysis. In terms of design, the tool adopts a security-centric approach, prioritizing principles like confidentiality, integrity, and availability. This approach ensures that the tool is resilient against potential attacks, promoting secure design practices throughout its implementation.
Digital forensics & Red/Blue Team Practices Hands-on Training
This course offers a practical encounter with a Red Team/Blue Team exercise, wherein the Red Team consists of offensive security experts endeavoring to breach the cybersecurity defenses of a given subject. Simultaneously, the Blue Team is responsible for defending against and responding to the attacks launched by the Red Team. The primary objective of this exercise is to tackle key issues, including identifying misconfigurations and coverage gaps in existing security products, enhancing network security to detect targeted attacks and reduce response time, raising awareness among participants about human vulnerabilities that could compromise system security, and developing the skills and maturity of the training group’s security capabilities within a secure, low-risk training environment.