Cybersecurity
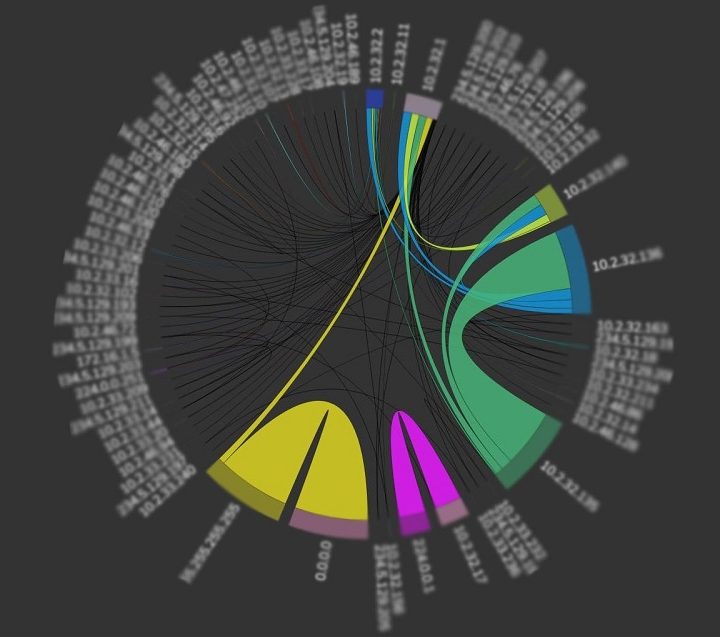
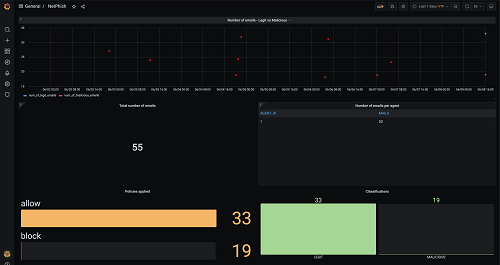
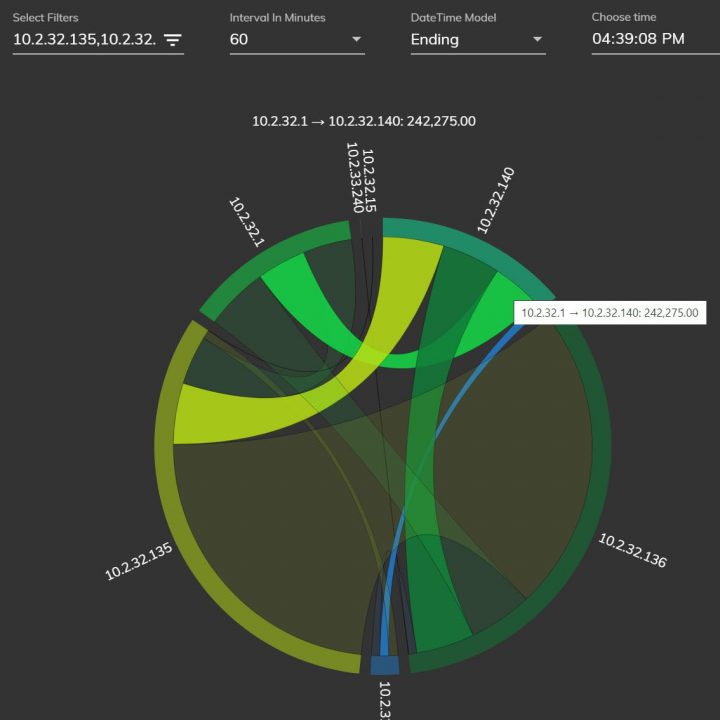
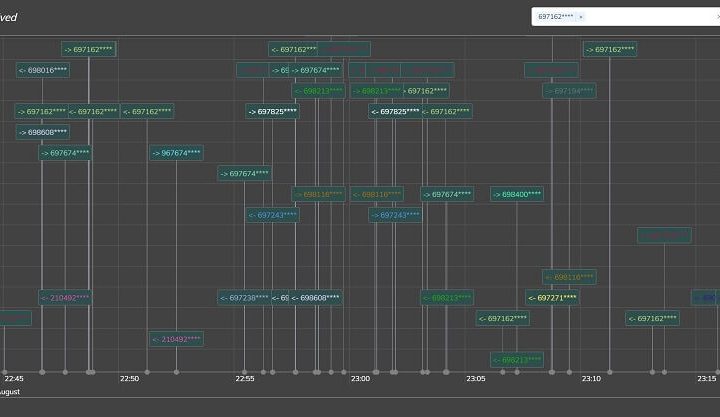
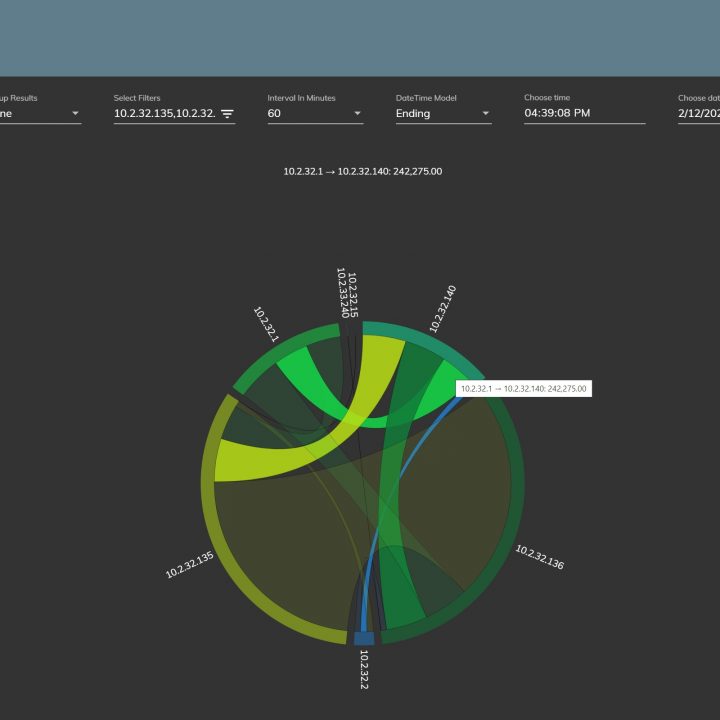
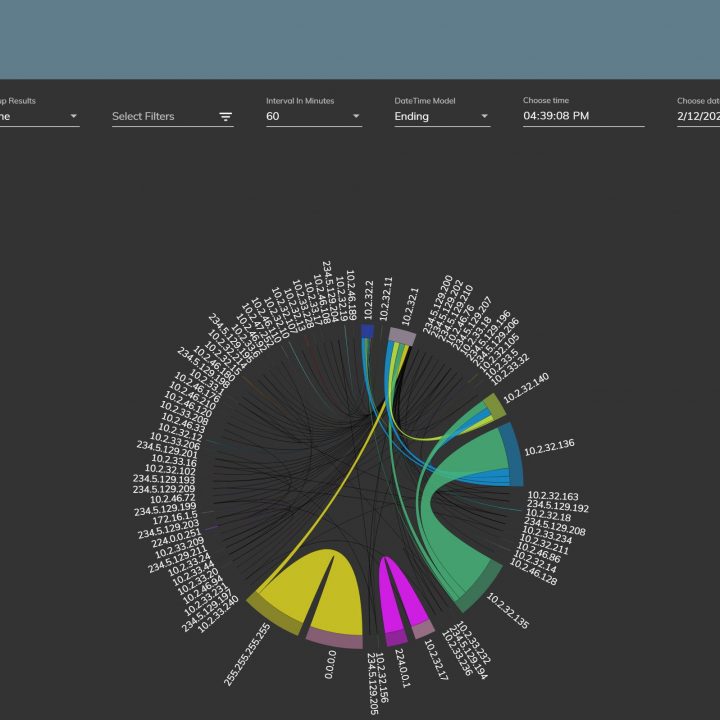
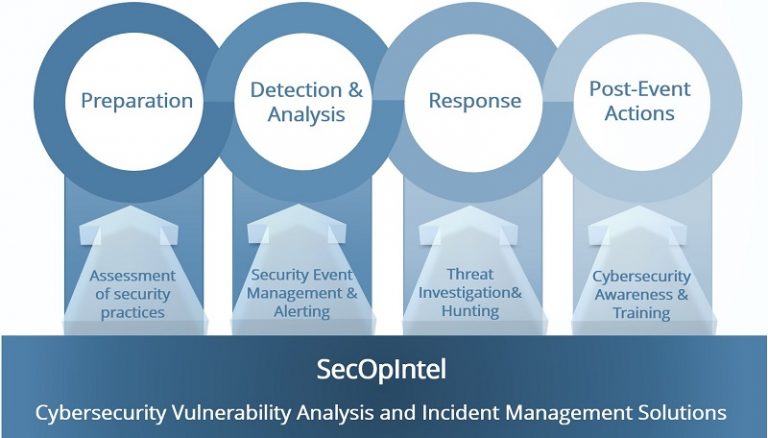
Zelus focuses on services promoting security-related Situational Awareness, incident management and threat hunting. Our cybersecurity services are targeting security analysts, consultants and IT infrastructure operators in general. They span from collection and analysis systems for digital forensic investigations to holistic cybersecurity deployments including security information and event management (SIEM), endpoint protection (EDR) and privacy preserving systems. Focusing on Security by Design, we build on our tested tools, i.e. Digital Forensics Toolkit and SecOpIntel, to develop a customised solution that will enable our customers realise a secure operating environment for their IT infrastructure.